What exactly happens?
Seeing this question for the first time, I thought I knew exactly what happens, I thought it was like finding a prince in a Nollywood movie.
 Don't mind me, it so easy for poor girls to find a rich prince in a nollywood movie, so I thought whatever was happening when I typed Google.com was super easy. I got to realize what I knew was just a tip of the iceberg. I was about to discover a whole lot of brand new things. I wanted to learn what exactly was happening behind the scenes (backend) when you type a URL (uniform resource locator) in a browser and share this discovery with you.
Don't mind me, it so easy for poor girls to find a rich prince in a nollywood movie, so I thought whatever was happening when I typed Google.com was super easy. I got to realize what I knew was just a tip of the iceberg. I was about to discover a whole lot of brand new things. I wanted to learn what exactly was happening behind the scenes (backend) when you type a URL (uniform resource locator) in a browser and share this discovery with you.
What happens behind the scenes?
 Understanding the client-server model is essential before delving into the specifics of the web infrastructure. The World Wide Web's (WWW) network is divided into servers, which store and manage the majority of data processing, and clients, which request data. A browser, for instance, is a client, and a server is the program that delivers data to that client. It's just like ordering a box of chocolate from Shoprite and getting it delivered to your doorstep. In this example shoprite is the server while the person who placed the order(customer) is the client.
Understanding the client-server model is essential before delving into the specifics of the web infrastructure. The World Wide Web's (WWW) network is divided into servers, which store and manage the majority of data processing, and clients, which request data. A browser, for instance, is a client, and a server is the program that delivers data to that client. It's just like ordering a box of chocolate from Shoprite and getting it delivered to your doorstep. In this example shoprite is the server while the person who placed the order(customer) is the client.
Domain Name System(DNS)
 The name of the website (URL) as well as the specific IP address to which it links are kept in a database called the DNS. As a result, when we enter the URL Google.com into our web browser, DNS matches the URL to Google's unique IP address. Yes! This simply means that we can also search for a URL page using the browser's IP address.
To put it another way, DNS is a list of URLs and their IP addresses, similar to how a phone book is a list of names and the phone numbers that go with them.
The name of the website (URL) as well as the specific IP address to which it links are kept in a database called the DNS. As a result, when we enter the URL Google.com into our web browser, DNS matches the URL to Google's unique IP address. Yes! This simply means that we can also search for a URL page using the browser's IP address.
To put it another way, DNS is a list of URLs and their IP addresses, similar to how a phone book is a list of names and the phone numbers that go with them.
Protocols: TCP/IP
We talked about how IP addresses are actually represented by domain names, but the Internet uses more than just IP. TCP/IP (TCP stands for Transmission Control Protocol) is a common name for the Internet Protocol Suite, which also includes other types of protocols. It is a set of rules that tell servers and clients how to talk to each other over the network and how data should be sent, received, broken up into packets, etc.
The Firewall
 Servers frequently come equipped with a firewall to guard against attacks and hackers. A firewall is a piece of software that regulates who can enter and leave a particular part of a network. In our example, when a browser requests the website at 216.58.223.196, a firewall must process the request to determine whether it is safe or poses a security risk to the server. A firewall can also be installed in the browser to determine if the IP provided by the DNS request is malicious.
Servers frequently come equipped with a firewall to guard against attacks and hackers. A firewall is a piece of software that regulates who can enter and leave a particular part of a network. In our example, when a browser requests the website at 216.58.223.196, a firewall must process the request to determine whether it is safe or poses a security risk to the server. A firewall can also be installed in the browser to determine if the IP provided by the DNS request is malicious.
Encryption and safety: HTTPS/SSL
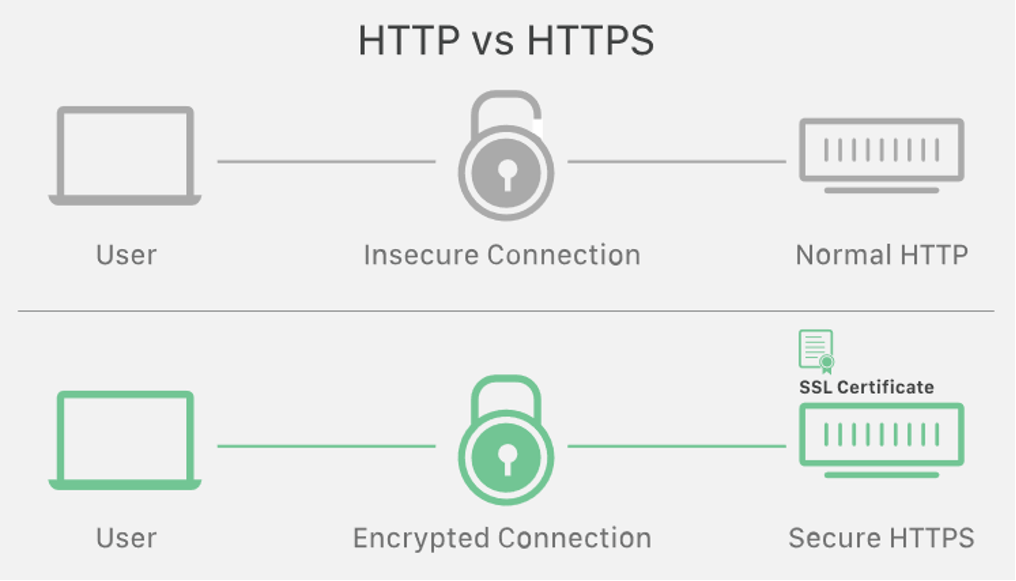 Now that the browser has the IP address, it will handle the https:// part of the URL. HyperText Transfer Protocol Secure, or HTTPS, is a secure variant of the standard HTTP protocol. The various types of requests and responses sent to clients and servers over a network are defined by this transfer protocol. To put it another way, it is the most common means of moving data between a browser and a website. GET, POST, and PUT are just a few of the HTTP and HTTPS requests. Because the HTTPS requests and responses are encrypted, users can rest assured that no third parties can steal or use their data.
Now that the browser has the IP address, it will handle the https:// part of the URL. HyperText Transfer Protocol Secure, or HTTPS, is a secure variant of the standard HTTP protocol. The various types of requests and responses sent to clients and servers over a network are defined by this transfer protocol. To put it another way, it is the most common means of moving data between a browser and a website. GET, POST, and PUT are just a few of the HTTP and HTTPS requests. Because the HTTPS requests and responses are encrypted, users can rest assured that no third parties can steal or use their data.
Load-balancer
 As previously stated, websites are hosted on servers. It would be impossible to host all of a website's traffic on a single server for most websites. Additionally, it would result in a Single Point of Failure (SPOF), as a single attack on that server would be all that was required to bring down the entire website.
Websites started using load-balancers, increasing the number of servers they have, clustering them, and increasing their availability and security. A piece of software known as a load-balancer uses a load-balancing algorithm to distribute network requests among several servers. The round-robin algorithm, which evenly and consequentially distributes requests among all servers, and the least-connection algorithm, which distributes requests based on the current server loads, are two examples of load balancer algorithms that we can use. HAproxy is a well-known load balancer.
As previously stated, websites are hosted on servers. It would be impossible to host all of a website's traffic on a single server for most websites. Additionally, it would result in a Single Point of Failure (SPOF), as a single attack on that server would be all that was required to bring down the entire website.
Websites started using load-balancers, increasing the number of servers they have, clustering them, and increasing their availability and security. A piece of software known as a load-balancer uses a load-balancing algorithm to distribute network requests among several servers. The round-robin algorithm, which evenly and consequentially distributes requests among all servers, and the least-connection algorithm, which distributes requests based on the current server loads, are two examples of load balancer algorithms that we can use. HAproxy is a well-known load balancer.
The Web server
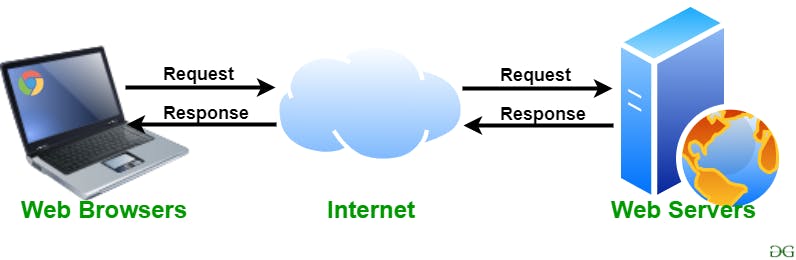 After the requests have been evenly distributed among the servers, one or more web servers will process them. A piece of software known as a web server is responsible for serving static content, such as plain text files, images, or basic HTML pages. Web servers like Nginx and Apache are two examples. Finding and serving the static content that corresponds to the requested address as an HTTP or HTTPS response is the responsibility of the web server.
After the requests have been evenly distributed among the servers, one or more web servers will process them. A piece of software known as a web server is responsible for serving static content, such as plain text files, images, or basic HTML pages. Web servers like Nginx and Apache are two examples. Finding and serving the static content that corresponds to the requested address as an HTTP or HTTPS response is the responsibility of the web server.
The Application server
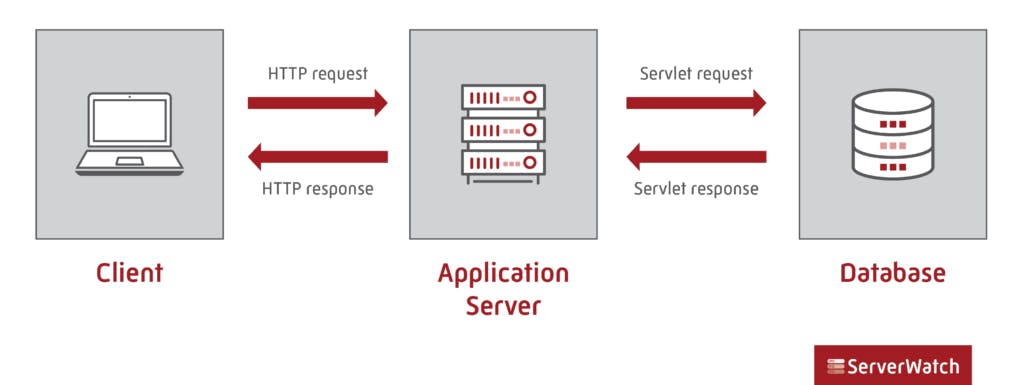 Every web page is built on top of a web server. However, most websites are dynamic, so they do not just want a page without any interaction. This indicates that one is capable of interacting with the website, saving information there, logging in with a user name and password, and other activities.
Every web page is built on top of a web server. However, most websites are dynamic, so they do not just want a page without any interaction. This indicates that one is capable of interacting with the website, saving information there, logging in with a user name and password, and other activities.
The Data Base Management System (DBMS)
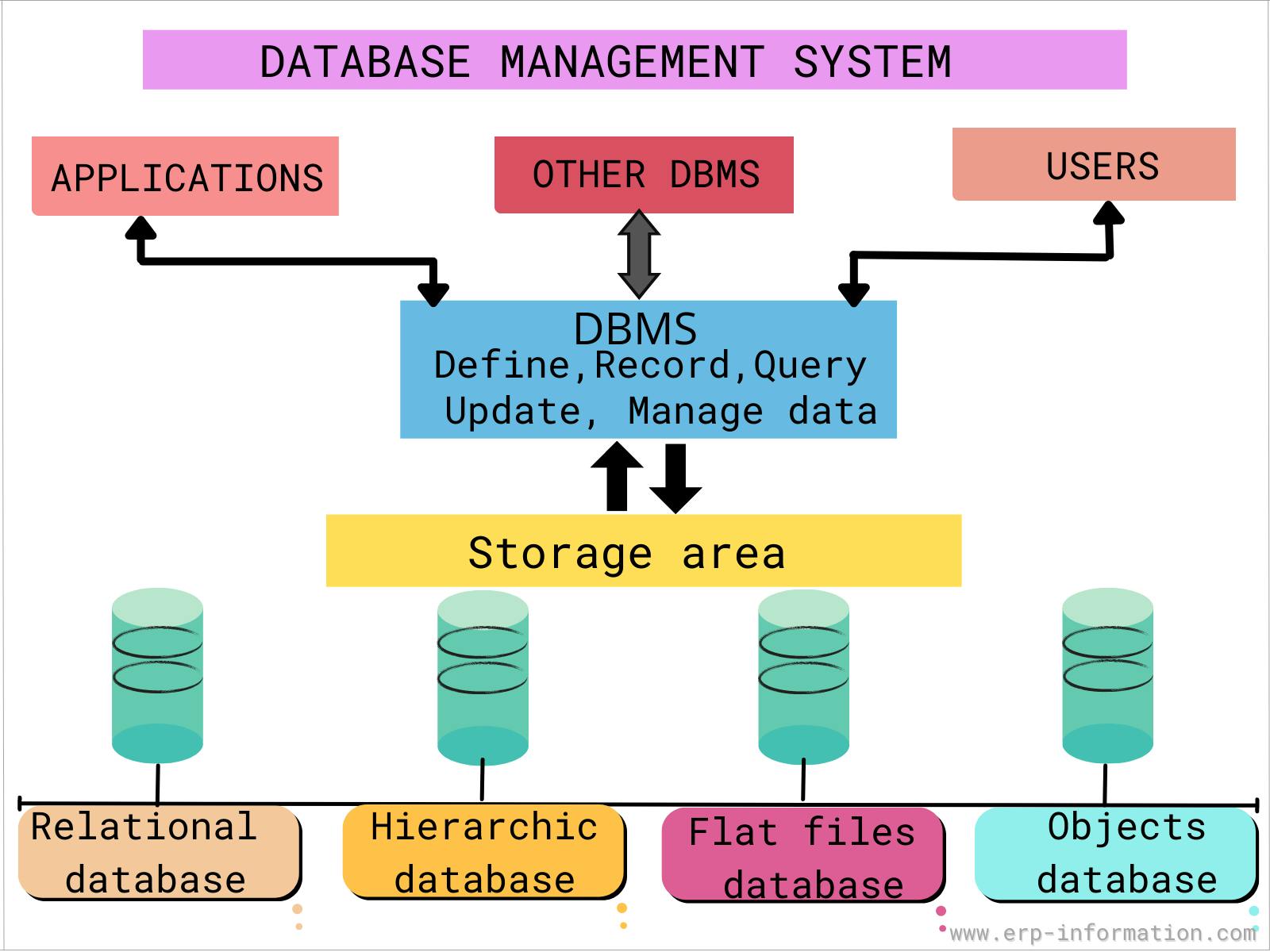 This is the final component of our web infrastructure. The DBMS is the program that will interact with the database to retrieve, add, and modify data. A database is a collection of data.
Database models are available in a variety of forms. Relational databases and non-relational databases are the two main types. A relational database can be thought of as a collection of tables that represent objects, with each row representing an instance of that object and each column representing an attribute. On those databases, we are able to execute SQL (Structured Query Language) queries. Relational databases like MySQL and PostgreSQL are popular choices because the data that is added to a non-relational database does not have to adhere to a specific schema, it can take many different forms. We can use NoSQL (MongoDB) here.
This is the final component of our web infrastructure. The DBMS is the program that will interact with the database to retrieve, add, and modify data. A database is a collection of data.
Database models are available in a variety of forms. Relational databases and non-relational databases are the two main types. A relational database can be thought of as a collection of tables that represent objects, with each row representing an instance of that object and each column representing an attribute. On those databases, we are able to execute SQL (Structured Query Language) queries. Relational databases like MySQL and PostgreSQL are popular choices because the data that is added to a non-relational database does not have to adhere to a specific schema, it can take many different forms. We can use NoSQL (MongoDB) here.
Conclusion
You can see the different processes that runs behind the scenes while we try to search for a particular website. This tells us how powerful technology is and how fast the computer is in processing information as it only takes miliseconds for it to display the searched website in proper conditions and strong internet connection.
 So when next you try to type Google.com remember the computer has so many activities going on behind the scenes.
So when next you try to type Google.com remember the computer has so many activities going on behind the scenes.
